Cybersecurity Maturity Model Certification (CMMC) 2.0 Compliance Services
Achieve CMMC 2.0 compliance with expert guidance from Petronella Technology Group— a Certified CMMC Registered Provider Organization (RPO). Stay eligible for Department of Defense (DoD) contracts, protect sensitive data, and future-proof your business.
What is CMMC 2.0?
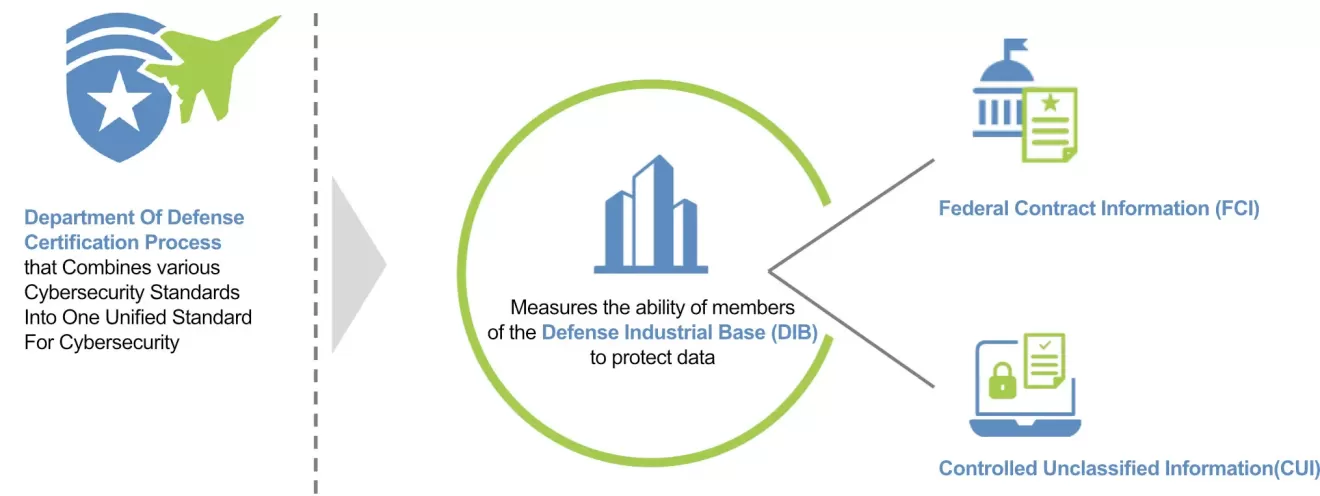
The Cybersecurity Maturity Model Certification (CMMC) 2.0 is the Department of Defense’s unified standard for implementing cybersecurity across the Defense Industrial Base (DIB). It simplifies the original five-tier model into three streamlined levels, aligning closely with NIST SP 800-171 and SP 800-172.
Understanding the 3 CMMC 2.0 Maturity Levels
 |
|
CMMC Maturity Model Overview
DFARS Compliance and SPRS Score Requirements
| "CMMC is the gateway to DoD contracts." |
Key DFARS Clauses:
SPRS Submission Portal: https://www.sprs.csd.disa.mil/ |
Why the Urgency? Your Contracts Depend on It
- Hackers actively target the defense supply chain — and DoD expects contractors to be proactive.
- Non-compliance may result in loss of eligibility or contract termination.
- False SPRS claims can trigger False Claims Act investigations and civil penalties.
- CMMC will be fully enforced soon — preparation is no longer optional.
POA&Ms, Waivers, and Assessment Tiers
- POA&Ms Allowed: CMMC 2.0 permits non-critical controls to be resolved post-assessment (must be completed within 180 days).
- No POA&Ms for Critical Controls: High-weighted practices must be fully implemented at time of audit.
- Self-Assessments: Required annually for Level 1 and some Level 2 contractors (low risk).
- Third-Party Assessments: Level 2 contractors handling CUI typically require triennial audits by a Certified 3rd Party Assessment Organization (C3PAO).
- Government Assessments: Level 3 contractors must pass a DIBCAC-conducted assessment.
- Waivers: Rarely granted and only by the DoD — contractors cannot request waivers themselves.
Key Benefits of CMMC 2.0 & NIST 800-171 Compliance
|
|
|
Strategic Takeaways from CMMC 2.0
- POA&Ms give some flexibility — but only for non-critical controls.
- SPRS scores are now required in most RFPs — submit yours today.
- CMMC certification can unlock higher-value defense opportunities.
- Primes will demand proof of flow-down compliance from subcontractors.
- Annual affirmations and continuous monitoring are not optional — they’re the new norm.
CMMC 2.0 Compliance for DoD Contractors
Cybersecurity Maturity Model Certification (CMMC) 2.0 compliance is now a critical requirement for companies in the Defense Industrial Base (DIB) that handle sensitive federal information. If your organization contracts with the U.S. Department of Defense (DoD) or hopes to, you must meet specific cybersecurity standards to secure those contracts. CMMC 2.0 is not just a checkbox exercise – it’s a framework designed to protect national security by safeguarding Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) on contractor systems. Achieving compliance can be complex, but it is vital for maintaining eligibility for DoD work, avoiding legal penalties, and defending against cyber threats.
Petronella Technology Group is here to help you navigate CMMC 2.0 with confidence. As a CMMC-Accredited Registered Provider Organization (RPO) with Certified CMMC Practitioners on staff, we guide defense contractors through every step – from understanding requirements to preparing for audits – so you can focus on your business. This comprehensive guide will cover everything you need to know about CMMC 2.0 compliance, including:
- CMMC 2.0 structure and requirements (Levels 1–3)
- The importance of compliance for DoD contractors
- How CMMC aligns with NIST SP 800-171 and NIST SP 800-172 frameworks
- Key DFARS cybersecurity requirements and regulations
- Definitions and implications of FCI and CUI
- The role of the Supplier Performance Risk System (SPRS) in compliance
- CMMC assessment processes (self-assessments, C3PAOs, DIBCAC audits)
- Use of POA&Ms (Plans of Action & Milestones) and waivers under CMMC 2.0
- A step-by-step guide to achieving compliance
- Common challenges in CMMC implementation (and how to overcome them)
- Benefits of becoming CMMC compliant
- Why Petronella Technology Group is the right partner for your CMMC journey
By the end of this guide, you’ll understand what it takes to meet CMMC 2.0 requirements and how to get there efficiently. Most importantly, you’ll see how a trusted partner like Petronella can streamline the process, helping you become certified on the first try and positioning your company for success in the defense sector.
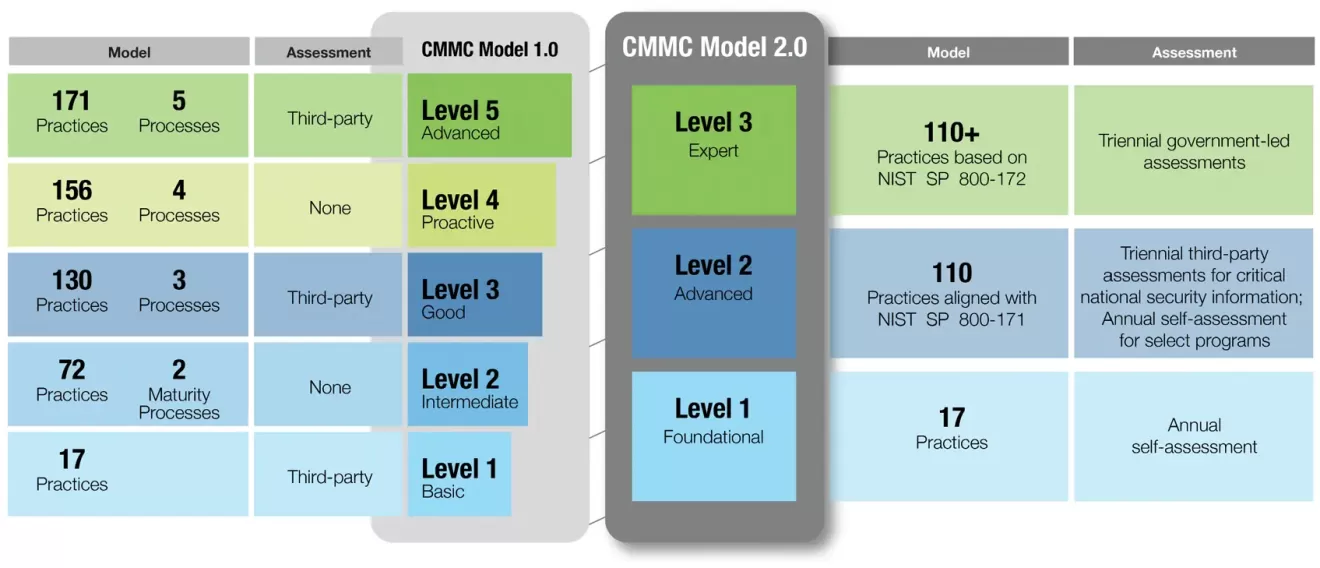
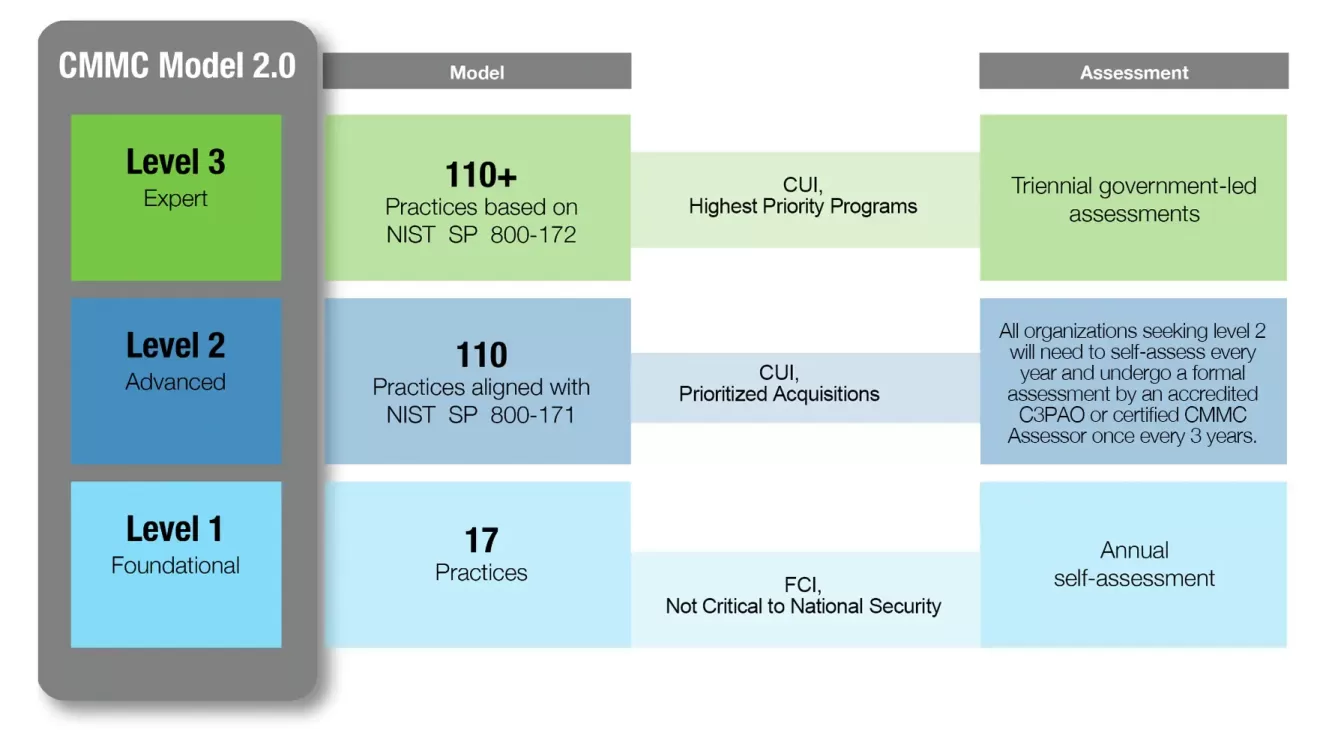
Understanding CMMC 2.0: Levels and Requirements
CMMC 2.0 simplifies the original five-level model into three maturity levels, each with a defined set of cybersecurity practices and assessment requirements. These levels build on one another, from basic cyber hygiene up to advanced protections against sophisticated threats. Below is an overview of CMMC Level 1, Level 2, and Level 3 and what is required for each:
- Level 1 (Foundational) – Basic Safeguarding of FCI. CMMC Level 1 focuses on basic cyber hygiene practices required to protect Federal Contract Information. This aligns with the 15 fundamental security controls specified in FAR 52.204-21 (the Federal Acquisition Regulation clause for basic safeguarding of contractor information systems). These practices include simple but crucial steps like using antivirus software, limiting system access to authorized users, and protecting media. Assessment: Level 1 requires an annual self-assessment – your organization must review itself against the 15 controls and affirm annually that all are implemented. A senior company official must sign off attesting to compliance, and the results of the self-assessment must be uploaded to the DoD’s SPRS database. No third-party audit is required for Level 1, but false attestation can carry serious legal risks. (Making a false claim of compliance is a serious offense under the False Claims Act and can lead to penalties.)
- Level 2 (Advanced) – Broad Protection of CUI. CMMC Level 2 is for contractors handling Controlled Unclassified Information – data that the government requires additional safeguarding (e.g. technical drawings, specifications, intellectual property related to defense). Level 2 compliance means implementing all 110 security requirements from NIST Special Publication 800-171 Rev. 2. NIST SP 800-171 is a detailed framework of cybersecurity controls (organized into 14 families) designed to protect CUI in non-federal systems. These controls cover areas like access control, incident response, configuration management, encryption, multi-factor authentication, and more. Assessment: For Level 2, the DoD will specify in each contract whether a self-assessment or a third-party assessment is required. In most cases involving CUI, a third-party CMMC assessment by an accredited C3PAO (Certified Third-Party Assessment Organization) will be required to formally certify compliance. Some less sensitive programs may allow self-assessment for Level 2, but in all cases you must undergo assessment at least every three years and submit the results to SPRS. Limited use of POA&Ms (remediation plans) is permitted at Level 2 (see more on POA&Ms below), but any critical requirements identified by the DoD cannot be postponed and must be fully met to achieve certification.
- Level 3 (Expert) – Expert Protection of CUI Against Advanced Threats. CMMC Level 3 applies to contractors working on the DoD’s highest-priority programs with the most sensitive CUI, especially information critical to national security. Level 3 builds upon Level 2 by requiring all the same 110 NIST SP 800-171 controls plus additional advanced practices from NIST SP 800-172. NIST SP 800-172 is a set of enhanced security requirements intended to defend against Advanced Persistent Threats (APTs) – highly skilled adversaries like nation-state hackers. The CMMC program has defined 24 specific requirements from NIST SP 800-172 that Level 3 companies must implement, such as more rigorous incident response, hunt operations, and robust risk management processes. Assessment: Level 3 certification will be conducted via a government-led audit by the Defense Contract Management Agency’s DIBCAC (Defense Industrial Base Cybersecurity Assessment Center) team. Before you can even go for Level 3, you’ll need to have already achieved a Level 2 certification by a C3PAO. Like Level 2, the certification is valid for three years, with annual affirmations required to ensure you maintain those stringent controls. POA&Ms are allowed for some non-critical items at Level 3 but must be resolved within 180 days, and waivers (if any) would be extremely rare (more on waivers later).
Key point: Each CMMC level builds on the one before – so a company at Level 3 meets all Level 2 and Level 1 requirements as well. Under CMMC 2.0, maturity processes (like documentation of process institutionalization) are no longer separately assessed at Level 1 and 2 as they were in the old model; the focus is purely on implementing the required practices. The result is a streamlined model: Level 1 for basic FCI protection, Level 2 for standard CUI protection (aligned to NIST 800-171), and Level 3 for enhanced protection against the most advanced threats (adding select 800-172 controls). Depending on the sensitivity of information you handle, the DoD will specify one of these levels in your contract, and you must be certified at that level to win or renew the work.
Why CMMC Compliance Matters for DoD Contractors
If you are a defense contractor or subcontractor, CMMC compliance is mission-critical. The DoD is integrating CMMC requirements into contracts to ensure the entire supply chain – from prime contractors down to small subcontractors – maintains adequate cybersecurity. Here’s why compliance is so important:
- Contract Eligibility: Soon, you will not be awarded DoD contracts unless you have the required CMMC certification (or at least an uploaded self-assessment for certain cases). According to the DoD, solicitations involving CUI or FCI will include a CMMC requirement that contractors “must meet to be eligible for contract award”. In other words, if a Request for Proposal (RFP) calls for CMMC Level 2, you must demonstrate Level 2 compliance or you cannot win the contract. This makes CMMC a gatekeeper for revenue – compliance is literally the price of admission to DoD opportunities. Companies that fail to comply risk being disqualified from bids or even losing current contracts.
- Legal and Regulatory Requirement: CMMC didn’t come out of thin air – it builds on existing laws and regulations, especially the DoD’s DFARS (Defense Federal Acquisition Regulation Supplement) clauses. Since 2017, DFARS 252.204-7012 has required defense contractors to implement NIST 800-171 to protect CUI. More recently, DFARS 252.204-7019 and 7020 (the “interim rule”) mandate that contractors self-assess and report their NIST 800-171 compliance scores in SPRS to even be considered for contracts. And DFARS 252.204-7021 will require the appropriate CMMC certification level once the CMMC rule is fully implemented. In short, cybersecurity compliance is already a legal requirement under DFARS, and CMMC is how DoD will verify and enforce it going forward. Noncompliance can lead to breach of contract, termination for default, and liability under the False Claims Act if a contractor misrepresents its cybersecurity posture.
- Protection of Sensitive Data: DoD contractors often work with sensitive technical data, specifications, mission plans, or personal data that, while unclassified, could be very damaging in adversaries’ hands. Compliance with frameworks like NIST 800-171 reduces the risk of breaches. Data exfiltration by hackers is a real threat to national security and to your business. A single cyber incident could not only jeopardize military programs but also tarnish your company’s reputation and result in costly remediation. By adhering to CMMC’s security controls, you greatly strengthen your cyber defenses. In fact, each CMMC level’s controls are designed to mitigate a specific range of threats – from basic malware and phishing at Level 1 to advanced nation-state tactics at Level 3. Compliance therefore directly correlates with better security.
- Competitive Advantage: Achieving CMMC compliance ahead of your competitors can be a significant market differentiator. Many contractors are procrastinating or struggling with implementation – if you get certified now, you can market your company as a trusted, DoD-ready supplier. Prime contractors in particular will prefer subcontractors who are already compliant to reduce risk in their supply chain. Also, compliance can open the door to new contracts that were previously out of reach. Conversely, not being compliant will soon become a competitive disadvantage, as compliant rivals will snap up contracts you can’t even bid on.
- Avoiding Penalties and Disruptions: The U.S. Department of Justice has launched a “Civil Cyber-Fraud Initiative” to pursue contractors who falsely claim to meet cybersecurity requirements. This means if you self-attest to controls or report a perfect SPRS score but have not actually implemented the requirements, you could face investigations, financial penalties, and False Claims Act lawsuits. Additionally, DoD may conduct spot-check assessments (through DIBCAC) of contractors’ 800-171 implementations under DFARS 7020. The safest course is to truly comply – not just on paper – and be ready to provide evidence of compliance. CMMC’s third-party audit requirement (for most cases) adds assurance that companies are doing more than lip service. By investing in compliance, you avoid the nightmare of contract interruptions, legal battles, or emergency scrambles to fix security gaps under the gun.
In summary, CMMC compliance is essential for anyone in the defense supply chain. It’s about keeping your contracts, staying on the right side of the law, and protecting the sensitive data entrusted to you. The DoD views cybersecurity as foundational to acquisition, much like quality control or safety. Contractors who take this seriously will thrive; those who don’t will be left behind or face dire consequences.
Pro Tip: Don’t wait for CMMC requirements to appear in your contract. Compliance is already expected now under DFARS 7012/7019. Every day of delay is risky. If you’re unsure where to start, consider reaching out for a free consultation with Petronella’s CMMC experts. We can assess your current state and help you develop a plan before it impacts your contracts.
How CMMC Relates to NIST SP 800-171 and 800-172
The backbone of CMMC 2.0’s requirements is formed by two key NIST publications:
- NIST SP 800-171 (Rev. 2) – “Protecting Controlled Unclassified Information in Non-Federal Systems and Organizations.” This document contains the 110 security requirements that are the core of CMMC Level 2. These 110 requirements are grouped into 14 families of controls (such as Access Control, Incident Response, Configuration Management, Media Protection, etc.). NIST 800-171 was specifically developed to help federal agencies ensure that contractors protect CUI. If your organization handles CUI, you are likely already contractually required to follow NIST 800-171 via DFARS 252.204-7012. CMMC Level 2 basically says: prove that you’re following NIST 800-171. It adds an assessment requirement to verify implementation of those controls. In practice, achieving Level 2 means developing a System Security Plan (SSP) mapping how you implement each of the 110 requirements, fixing any gaps, and being prepared to show an assessor evidence for each item. NIST 800-171 focuses on safeguarding information from a wide array of threats, and is considered a baseline cybersecurity standard for defense contractors.
- NIST SP 800-172 – “Enhanced Security Requirements for Protecting CUI.” This is an overlay on top of 800-171, intended for critical programs facing Advanced Persistent Threats. Think of 800-172 as extra credit controls to further harden systems that absolutely cannot be compromised. CMMC Level 3 will require a subset of these 800-172 controls (24 of them, per DoD’s current plan). Examples of NIST 800-172 enhanced requirements include things like employing deception technologies to detect attackers, conducting rigorous penetration testing, monitoring insider threats, and other proactive defense measures beyond the basics. These controls assume the adversary is sophisticated and already inside or actively targeting your systems, and focus on limiting the damage they can do. For most contractors, Level 3 and NIST 800-172 will not be required – it’s reserved for the elite few working on the crown jewels of DoD programs. But even those aiming for Level 2 can appreciate that NIST 800-172 represents best practices for a high-security environment. By understanding which additional practices might be required at Level 3, companies can better anticipate future needs if their work becomes more sensitive.
It’s worth noting that both 800-171 and 800-172 are derived from the broader NIST SP 800-53 catalog of controls (used by federal agencies). So if you are familiar with other standards like FedRAMP or even ISO 27001, you’ll see a lot of overlap. The key difference is that 800-171 is tailored to protecting CUI specifically and assumes the organization is not a federal agency (so it excludes things the government does internally and focuses on contractor systems).
In summary, CMMC is essentially the DoD’s way of enforcing NIST standards in the defense contractor community. Level 2 = “implement NIST 800-171 and prove it,” Level 3 = “implement NIST 800-171 plus the specified 800-172 enhancements and prove it.” If you master NIST 800-171’s requirements, you are most of the way to CMMC compliance. And if Level 3 is in your sights, start looking at NIST 800-172’s guidance on advanced cyber defenses. Petronella’s team has deep expertise in these NIST frameworks and can help translate them into actionable controls for your business.
Understanding DFARS and Other DoD Cyber Regulations
The DoD’s cybersecurity requirements for contractors are codified in a series of DFARS clauses (Defense Federal Acquisition Regulations Supplement). CMMC was born out of these requirements to ensure they are actually being met. Here are the key regulations and how they tie in:
- DFARS 252.204-7012 – Safeguarding Covered Defense Information and Cyber Incident Reporting: This clause, in effect since 2017, requires contractors to implement the NIST SP 800-171 controls whenever Covered Defense Information (which includes CUI) is present, and to rapidly report any cyber incidents to the DoD. Essentially, if your contract involves CUI, you must have “implemented, or have an actionable plan to implement, the security requirements specified by NIST SP 800-171” and report breaches within 72 hours. DFARS 7012 is why NIST 800-171 became a household name in defense contracting – it made those 110 controls a mandatory part of contracts (even before CMMC). Importantly, DFARS 7012 also requires you to flow down these requirements to your subs and to create an incident response plan.
- DFARS 252.204-7019 – Notice of NIST SP 800-171 DoD Assessment Requirements: This clause (effective since late 2020) requires contractors to conduct a self-assessment of their NIST 800-171 implementation and upload a summary score into the Supplier Performance Risk System (SPRS). The DoD created a scoring methodology (giving a maximum score of 110 if all controls are implemented, with points deducted for any incomplete items). Every contractor needs to have a current Basic Assessment score on record in SPRS, updated at least every 3 years, to be considered for new awards. In practice, this means if an RFP includes DFARS 7019 (which most now do), you must log into the SPRS web portal and submit your score and basic information about your assessment (like date and scope). Contracting officers can check SPRS to see if you have a valid score on file and can withhold awards if you don’t. DFARS 7019 basically set the stage for CMMC by encouraging contractors to assess themselves and report status.
- DFARS 252.204-7020 – NIST SP 800-171 DoD Assessment Methodology: This clause works with 7019. It says you agree to let DoD (i.e., DIBCAC or another authorized agency) come and perform a higher-level assessment of your 800-171 implementation if they choose. The DoD can conduct a Medium or High assessment (which are essentially deeper audits of your controls and evidence). It also requires you to fix any deficiencies found. 7020 is basically DoD’s ability to audit contractors on 800-171, even before CMMC formally kicks in, and to ensure the SPRS scores being reported are accurate. If DIBCAC shows up for a High assessment, they will want to see your SSP, policies, and technical configuration to confirm your self-attested score.
- DFARS 252.204-7021 – CMMC Requirement (coming soon): This clause is the one that will mandate CMMC certification. It isn’t fully in effect until the CMMC program’s rulemaking is completed (expected in 2024). Once active, it will require that contractors have a current CMMC certificate (not older than 3 years) at the level specified in the contract. Essentially, 7021 ties it all together – where 7012 said “implement 800-171,” 7019/7020 said “self-attest and let us review,” 7021 will say “get a formal CMMC certification to prove it.” DoD has indicated there will be a phased rollout over several years after the final rule, gradually adding CMMC requirements to more contracts. However, the bottom line is that CMMC is going to be woven into the DFARS fabric as a condition of doing business with DoD.
In addition to these, contractors should be aware of related regulations like FAR 52.204-21 (basic FCI safeguarding, which is basically CMMC Level 1), and any program-specific requirements that might impose extra controls. For example, some contracts might require compliance with ITAR (International Traffic in Arms Regulations) for certain data, or FedRAMP moderate if using cloud services to store CUI. But generally, if you meet CMMC (and thus NIST 800-171/172), you’ll satisfy most of these related obligations.
The main takeaway: The DFARS clauses are the “teeth” behind CMMC. They are in your contracts today. CMMC is the formal certification process that will verify you actually follow those clauses. Together, they aim to raise the bar across the defense industrial base so that security is consistently applied. From a practical perspective, use the DFARS requirements as a checklist: Have we done our SPRS self-assessment? Are we prepared for a DoD audit? Do we have an incident reporting procedure? Petronella helps clients ensure all these boxes are checked as part of our compliance readiness service.
FCI vs. CUI: Determining Your Required Level
A fundamental step in your CMMC journey is understanding what kind of information you handle – specifically, FCI versus CUI – because this determines which CMMC level you need.
- Federal Contract Information (FCI): This is information provided by or generated for the Government under contract that is not intended for public release. FCI is essentially any non-public info you get or create as part of doing work for the government, which isn’t strictly controlled as CUI. It could include things like the contents of a DoD purchase order, meeting minutes, project schedules, or basic deliverables that don’t contain sensitive data. Under FAR 52.204-21, all contractors must protect FCI with basic security measures (the 15 controls in Level 1). If FCI is the highest level of sensitive data you handle, the DoD will likely require CMMC Level 1 compliance for your contract. Even if CUI comes up in the future, every company that does any federal work should at least have those Level 1 safeguards in place.
- Controlled Unclassified Information (CUI): CUI is a broad category of data that the Government deems sensitive and requires safeguarding or dissemination controls pursuant to laws or regulations. There are dozens of CUI categories (e.g., export-controlled technical data, procurement sensitive information, critical infrastructure security data, personally identifiable information under privacy laws, etc.). What they have in common is that CUI requires protection at a higher level than FCI. If your contract or subcontract involves CUI, you will need to implement all NIST 800-171 controls and thus meet CMMC Level 2 or higher. The presence of CUI is the dividing line between Level 1 and Level 2. Examples: technical schematics for a weapons system, test results, software source code for a defense project, or even things like building facility plans for a military base could be CUI. The DoD will indicate in the contract if CUI is involved (often via a CUI attachment or in the statement of work). It’s crucial to identify all CUI in your environment, as many CMMC requirements (like access control and encryption) specifically target protecting that CUI.
Why it matters: If you underestimate and assume you only have FCI when in fact you have CUI, you might prepare for the wrong level of compliance. Conversely, if you assume everything is CUI and try to implement Level 2 for all systems, you might be doing more work (and spending more) than necessary. A best practice is to scope your environment: identify the systems and people that store or process CUI versus those that handle only FCI or public data. You can then limit where CUI lives (for instance, in a secure enclave or specific network segment) and reduce the boundary of what needs Level 2 controls.
In practical terms:
- If you are a contractor providing only commercial-off-the-shelf products or simple services with no sensitive data exchange, you might only need Level 1.
- If you receive any technical data, specifications, or reports from DoD that are marked as CUI (or that obviously contain sensitive details), plan for Level 2.
- Only if you work on extremely sensitive programs (often involving both unclassified and classified elements) would you ever need Level 3. In fact, Level 3 contracts will likely be explicitly designated by DoD – e.g. if you’re dealing with highly critical technologies or operating in environments where state-sponsored cyberattacks are an everyday concern.
Remember, CUI requires stricter security by definition. That’s why CMMC Level 2 maps to NIST 800-171, which was built to protect CUI. If unsure whether data you have is CUI, consult the DoD CUI Registry which lists all CUI categories, or ask your government contracting officer for clarification. Petronella can also assist in performing a data discovery to identify any CUI in your systems. Mis-classifying data can be costly, so it’s worth the due diligence.
The Role of the Supplier Performance Risk System (SPRS)
One acronym that keeps coming up is SPRS – the Supplier Performance Risk System. SPRS is a DoD web application where contractors’ compliance scores and other procurement risk information are stored. It plays a key role in current compliance efforts and will continue to in the CMMC era:
- Reporting NIST 800-171 Self-Assessments: As mentioned under DFARS 7019, contractors must submit their NIST 800-171 Basic Assessment scores to SPRS. This score ranges from -203 up to 110 (with 110 meaning all controls fully implemented, and lower scores indicating some controls are not yet in place). The scoring methodology penalizes missing controls; for example, not having multi-factor authentication might deduct 5 points. The score submission also includes the date of the assessment and a brief description (often an acknowledgement if there’s a Plan of Action for any gaps). If you don’t have a score in SPRS, you likely cannot win new DoD contracts. DoD acquisition officials use SPRS as a gate – proposals without a current score may be rejected as non-compliant. Therefore, even before CMMC assessments, doing that self-assessment and getting a score in SPRS is a must-do task.
- Visibility to DoD: SPRS is only accessible to DoD personnel and the contractor (you can see your own info, but not others’). DoD program managers and contracting officers use it to gauge the risk of awarding to a given company. A low SPRS score (far below 110) might raise red flags and trigger further questions or a decision to not award until issues are fixed. In some cases, agencies might favor contractors with higher scores if security is mission-critical. With CMMC, certified companies’ status will also be recorded (likely in SPRS or a related system like the CMMC Enterprise Mission Assurance Support Service, eMASS, for Level 2/3). So SPRS becomes the system-of-record for your cyber compliance status – first via self-assessments, and eventually via CMMC certifications and annual affirmations.
- Maintaining Your Score: Once you post a score, it isn’t “set and forget.” The score is valid for up to 3 years for DFARS purposes, but if you remediate items and improve, you can (and should) update it. Also, if you complete a formal assessment (e.g., a DIBCAC High assessment or a CMMC Level 2 certification), those results would supersede your self-score. Be honest in SPRS – if your score is 80, that’s okay as long as you have a Plan of Action to get to 110. Overstating your score (claiming 110 without evidence) can lead to big trouble if audited. The DoD has already pursued legal action against at least one contractor for false SPRS reporting.
- Integration with CMMC: As CMMC rolls out, expect RFPs to require not just an SPRS score but also a specific CMMC level certification. Likely, the SPRS record will note if you have a current CMMC certificate on file or not. In the interim, some solicitations might say “Offerors shall have a current NIST SP 800-171 DoD assessment (SPRS score) and be able to achieve CMMC certification within X time.” This was seen in the early CMMC pilot contracts. So, maintaining your SPRS score is part of proving you are “presently responsible” cybersecurity-wise.
Action Item: If you haven’t done so, perform a NIST 800-171 self-assessment and submit your SPRS score as soon as possible. Petronella can assist with the assessment methodology and calculation of your score. We ensure you understand any gaps (each missing control) and have a solid Plan of Action & Milestones (POA&M) to address them. Posting an honest score with a clear remediation timeline is far better than guessing or ignoring this requirement. Remember, SPRS is effectively Phase 1 of CMMC implementation – it’s how DoD is tracking compliance right now.
CMMC Assessment Process: Self-Assessment vs. C3PAO vs. DIBCAC
How do you actually get “CMMC certified”? The process depends on the level and the contract requirements:
- Self-Assessments (First-Party): For Level 1, and for certain Level 2 contracts designated as lower risk, the CMMC assessment can be done as a first-party self-assessment. This means your own organization examines each requirement, ensures it’s met, and a senior official signs an attestation of compliance. You then submit the self-assessment results (and affirmation) into SPRS. The self-assessment is essentially an honor system, though false statements are subject to False Claims Act penalties as noted. Self-assessments must be done annually for Level 1 (because things change fast in basic IT environments) and at least every 3 years for Level 2 self-attestation cases. Even in self-assessment, you should maintain thorough documentation (SSP, POA&M, training records, etc.) because the government can still decide to audit you (especially under DFARS 7020 or if something goes wrong). Self-assessment is less formal and costly than third-party, but it requires discipline to be objective. Petronella often helps companies by doing a readiness review – essentially acting like an outside assessor to double-check your self-assessment before you submit it, ensuring nothing critical is overlooked.
- Third-Party CMMC Assessments (C3PAO Audits): For most contracts involving CUI, especially those in the “Defense CUI Registry Grouping”, a C3PAO will be required. A Certified Third-Party Assessment Organization is a company authorized by the CMMC Accreditation Body (The Cyber-AB) to conduct official CMMC audits. These are the independent examiners who will validate that you meet all Level 2 requirements. The process works like this: once you believe you are ready, you engage a C3PAO (through the Cyber-AB marketplace). The C3PAO’s assessors will schedule an assessment, review your documentation, interview your staff, and test your security controls against the CMMC criteria. If all goes well, they will recommend you for certification, and you’ll receive a CMMC certificate for Level 2, valid for 3 years. If there are findings (some controls not met), you may get a chance to remediate (with POA&M) and undergo a targeted reassessment on those items. Third-party assessments are a bit like financial audits – they require preparation and can be rigorous. Petronella, as an RPO, cannot conduct a CMMC audit (we deliberately avoid conflicts of interest), but we can prepare you so thoroughly that passing the C3PAO audit is almost a formality. Our goal is that you go into the assessment with confidence, having all evidence and policies at your fingertips – so the audit goes smoothly and you “pass on the first try.”
- Government-led Assessments (DIBCAC): For Level 3 (Expert) and potentially in some special cases at Level 2, the DoD’s own assessors will conduct the audit. The Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), part of DCMA, has teams that have been doing High assessments for NIST 800-171 and will do Level 3 CMMC audits. A DIBCAC assessment is typically more in-depth and may span several days. They will expect not only technical compliance but that your organization has mature cybersecurity practices (e.g., continuous monitoring, proactive threat hunting as called for by some 800-172 controls). Also, as per CMMC rules, to even be assessed at Level 3, you must already have Level 2 certification by a C3PAO. So it’s a two-step: first a third-party certifies you have the basics, then the government validates the advanced stuff. DIBCAC may also do spot-checks of C3PAO assessments at Level 2 for quality purposes or if the contract is very sensitive. If you’re subject to a DIBCAC review, it’s the highest bar – but at that point, you’re among an elite set of contractors. Petronella can provide continuous compliance support to help you maintain readiness for such government audits, which can occur with relatively short notice.
- Assessment Scoping: All assessments (self, C3PAO, DIBCAC) will have a defined scope. This means they will look at specific networks, systems, and processes in your environment that handle FCI/CUI. It’s important to properly define and limit scope to what’s necessary. For instance, if only one business unit handles CUI, the assessment can be scoped to that unit’s IT systems rather than your entire enterprise. A good assessor will help confirm scope early on. Petronella assists clients in scoping to reduce complexity – e.g. perhaps moving CUI into a dedicated enclave system so that the rest of your corporate IT is out-of-scope. This can save time and cost when it comes to assessments.
- Certification and Maintenance: After a successful assessment, you’ll be granted a CMMC certification at the respective level. That certificate is typically valid for 3 years from date of issue. However, you must also annually affirm that you are still in compliance (basically self-confirm nothing has degraded) or the certification can lapse. If during the 3-year period you significantly change your systems or have a major incident, there may be requirements to inform DoD or even re-certify in some cases. Always keep your security up to date – passing the audit is not the end, it’s the beginning of continuous vigilance.
In summary, the assessment process is your “exam day.” Whether self or third-party, preparation is key. The better you map out requirements, implement controls, and gather evidence, the easier the assessment. Petronella’s approach includes pre-assessment checklists, mock interviews, and evidence reviews to ensure you are 100% ready for the real thing. We coordinate with reputable C3PAOs and can even be on-site during your assessment to help address any questions that arise.
Plans of Action & Milestones (POA&M) and Waivers in CMMC 2.0
Realistically, not every company will have 100% of controls in place by the time of assessment. Plans of Action and Milestones (POA&Ms) are a tool that allows you to address remaining gaps on a defined timeline. Under CMMC 1.0, POA&Ms were not allowed at all – you either were 100% compliant or you failed. CMMC 2.0 introduces some flexibility:
- Limited POA&M Use: For Level 2 and 3 assessments, you can be granted a “Conditional” certification if only a small number of requirements are not met, provided those are not on the DoD’s list of critical controls that cannot be delayed. If a POA&M is allowed, you will have 180 days to fix those items and undergo a POA&M closeout assessment to verify they’re now met. For example, if you had 3 low-risk controls not implemented, you could still get a conditional pass, immediately work on those 3 items, and have a C3PAO (or DIBCAC for Level 3) re-check just those items. If you succeed, you get a full certification valid for the remainder of the 3-year period. If you fail to close them in 180 days, your conditional status expires and you lose certification. Note: Level 1 does not allow POA&Ms at all – you must implement all 15 basic controls to be Level 1 certified.
- Critical Controls: The CMMC program has identified certain controls (likely those that are high-weight in the 800-171 scoring or considered fundamental, like having an up-to-date antivirus or enabling multifactor authentication) that cannot be on a POA&M. That means if you’re missing one of those, you won’t even get conditional approval – you’ll be failed outright until it’s fixed. The rationale is that some practices are too important to leave undone even for a short period. When preparing for an assessment, pay special attention to these critical items; knock them out first. Typically, these might include things like MFA (Control 3.5.3 in 800-171), disabling obsolete protocols, having an incident response plan, etc. Petronella can advise on which controls are considered “must-haves” to avoid POA&M issues.
- Waivers: CMMC 2.0 also contemplates a process for DoD to grant a waiver for the CMMC requirement in a specific contract, but this is expected to be extremely rare. A waiver would mean a contractor can be awarded the contract without a CMMC certification for a limited time, usually due to urgent national security needs. According to DoD guidance, waivers:
- Must be approved at a very high level (e.g., by an Under Secretary of Defense) and are initiated by the government program office, not the contractor.
- Are time-bound (e.g., 6 months) and do not excuse the contractor from implementing security requirements – they only delay the certification requirement. You’d still need to do everything in NIST 800-171; you just might get extra time to get the actual certificate.
- Will not be granted for Level 3 situations involving classified work or cleared contractors, and unlikely for most Level 2 cases either. Essentially, waivers are a last resort if there’s no other way to get a critical mission done.
- Are applied to an entire contract, not individual companies. So if a program gets a waiver, none of the performers need the cert for that period – but once it expires, everyone will need to have it.
The bottom line on waivers is: don’t count on one. The DoD has openly stated that contractors “should not rely on a potential waiver” and should pursue compliance as if waivers didn’t exist. Waivers are more about giving DoD flexibility in roll-out. From your perspective as a contractor, it’s far better to assume you will need to be certified and work towards that goal. If a waiver happens to cover you temporarily, great – but that’s icing on the cake, not a strategy.
In summary, POA&Ms provide a safety net for minor shortfalls, and waivers are a rare escape hatch for DoD in exceptional cases. Neither is an excuse to procrastinate or avoid doing the work. Use POA&Ms wisely as part of your planning: if certain upgrades or purchases can’t be done before the audit, document the plan, allocate the budget, and show that to the assessors. A well-crafted POA&M might convince an assessor to still recommend you (conditionally). Petronella assists clients in creating effective POA&Ms that satisfy CMMC requirements – including realistic milestones and resource commitments – and in prioritizing critical controls to minimize what ends up on a POA&M in the first place.
Step-by-Step Guide to Achieving CMMC Compliance
Achieving CMMC compliance can seem daunting, but breaking it down into clear steps will help you navigate the journey. Here’s a step-by-step guide:
- Determine Your Required CMMC Level: Start by identifying whether you handle only FCI or also CUI (and what type). Review your contracts and talk to your DoD customers to confirm what data you receive. If it’s just FCI, you’re aiming for Level 1. If any CUI is involved, you need Level 2. Only very select contractors will need Level 3 (usually you’d know because you work on high-security programs). Knowing your target level focuses your efforts.
- Scope Your Environment: Figure out where the FCI/CUI resides in your IT systems. Which networks, servers, laptops, cloud services, etc., process or store that data? This set of systems is your CMMC scope. Everything in scope must meet requirements. If possible, consider segmenting or isolating CUI into a specific enclave or set of systems – this way, you don’t have to upgrade every single corporate system to CMMC standards, only the ones in scope. For example, you might decide that only a secure cloud environment will host CUI, and users access it via dedicated laptops – that enclave would be in scope, while their normal business IT is out of scope. Scoping is critical to control costs and complexity.
- Perform a Gap Assessment (NIST 800-171 Assessment): Measure your current security controls against the requirements. If going for Level 1, check yourself against the 15 FAR 52.204-21 controls. For Level 2, perform a full NIST 800-171 self-assessment. This means reviewing all 110 requirements and marking each as “MET” or “NOT MET,” and scoring accordingly. Identify the gaps – e.g., you might find you lack multi-factor authentication (requirement 3.5.3) or haven’t encrypted all laptops (requirement 3.1.19). Also review your documentation: Do you have written policies for access control, incident response, etc.? Many 800-171 controls require written and implemented policies. Petronella often uses detailed checklists and the official DoD Assessment Methodology to conduct this gap analysis. The output is a list of remediation tasks.
- Develop a Plan of Action & Milestones (POA&M) and Budget: Based on the gaps identified, create a formal POA&M document. For each missing or deficient control, outline what needs to be done, who is responsible, and a target date. Prioritize high-impact items and any CMMC critical controls first. At the same time, estimate the resources needed – this could include purchasing software/tools (e.g. a SIEM for log monitoring), hiring staff or consultants for expertise, and time for implementation. Having a POA&M is not only good practice; it’s something you’ll likely need to show in the assessment if not everything is finished. This plan will guide your remediation phase. (If you are already close to compliant, your POA&M might be short. If you’re starting from scratch, expect a longer POA&M with many projects.)
- Implement the Required Controls: This is the main effort – execute the POA&M. It will involve a combination of technical, physical, and administrative changes:
- Technical controls: Installing or configuring security solutions like firewalls, multifactor authentication, encrypted storage, endpoint protection (EDR/antivirus), backup systems, etc., to meet the technical requirements.
- Policies and Procedures: Drafting or updating your System Security Plan (SSP) that describes your system and how each NIST 800-171 control is met. Also creating formal policies (acceptable use policy, incident response plan, configuration management policy, etc.) and procedures or runbooks for IT tasks. All policies should be approved by management and communicated to staff.
- Training and Awareness: Ensuring all employees (and especially IT administrators) are trained on their cybersecurity responsibilities. CMMC requires security awareness training (which maps to 800-171 control AT family) – make sure you conduct this and document it. Petronella provides tailored CMMC role-based training (e.g., training for general users vs. IT staff) to meet these requirements and build a security-first culture.
- Remediation of weaknesses: Fixing any open vulnerabilities discovered. For example, if your gap assessment found that patches were not up to date, implement a robust patch management routine and get systems updated. If default passwords were still present on some systems, eliminate those. Essentially, close every gap identified and then some – aim not just for bare minimum, but a solid security posture.
- Throughout this phase, keep evidence. Document configurations, take screenshots, maintain change logs, save training sign-in sheets, etc. This documentation will be gold during your assessment to prove each control is in place.
- Conduct an Internal Pre-Assessment: Once you believe all requirements are met (or all critical ones, with POA&M for any minor leftovers), do a mock assessment. Pretend you are the C3PAO auditor: review each of the 110 (or 15) practices and verify you have proof for each. Test your team’s knowledge – e.g., can they locate the Incident Response Plan quickly and do they know their role in it? This internal audit will surface any lingering issues. It’s often helpful to have a fresh set of eyes for this – Petronella’s consultants frequently perform these pre-assessments as a final check. We might use the official CMMC Assessment Guide as a rubric to ensure you’re hitting all the objectives.
- Submit SPRS Score and Prepare Certification Request: Before the formal assessment, make sure your SPRS score is updated to reflect your current state. If you’ve achieved 110/110 in practice, your score should be 110 (or very close). If not, ensure the score posted matches your implemented controls and note in SPRS that a POA&M exists for the remainder. Then, if a third-party assessment is needed, coordinate with the CMMC Cyber-AB Marketplace to select a C3PAO and schedule your certification assessment. (For Level 1, you won’t need a C3PAO – you would just finalize your self-assessment and affirmation in SPRS and you’re essentially done, though you might internally decide to have a consultant review it.)
- Undergo the CMMC Assessment: This is the formal audit by the C3PAO or DIBCAC. Provide them the requested documentation (usually they’ll ask for your SSP, policies, network diagrams, asset inventories, etc. ahead of time). Then be ready during the assessment days to show evidence of each control’s implementation. The assessors will likely interview various personnel (IT staff, security officer, management, even random employees to confirm security awareness). They may also inspect systems or settings (for instance, checking that an account gets locked after 3 failed logins, or that your server has the required configurations). With thorough preparation, this process should go smoothly. If an issue is found, don’t panic – often you can correct minor findings on the spot or provide additional evidence. At the end, the assessor will either say you met all requirements (congratulations, you’ll be recommended for certification) or that you have some deficiencies. If deficiencies exist, they’ll either halt certification until those are fixed, or in limited cases allow a POA&M/conditional pass. Work closely with the assessor – they will explain what needs to be done.
- Close Out POA&Ms and Get Certified: If you had any outstanding items, address them immediately and have the assessor verify closure. Once all requirements are met, the C3PAO submits their report to the CMMC governing body, and you receive your CMMC certificate for the level achieved! Now you can provide that certification information to contracting officers as needed (though DoD will also have it on record).
- Maintain and Monitor: Compliance doesn’t end with certification. You should integrate CMMC practices into your day-to-day operations. Continue to monitor your systems (through log reviews, automated tools, etc.), keep up with patches, conduct regular training, and annually re-assess yourself. Also each year, remember to have a senior executive submit the annual affirmation in SPRS that you’re still in compliance. If you make major changes (e.g., move to a new IT system or cloud provider), update your SSP and be sure the new environment is compliant too. Set reminders for a few months before your 3-year mark to start planning for re-certification. If you stay ready, you won’t have to scramble later.
Each of these steps can be a project in itself, but with a structured approach, you can tackle CMMC methodically. Many companies start by addressing the “low-hanging fruit” (easy fixes) while simultaneously planning for bigger changes (like migrating to a secure cloud enclave). The key is leadership commitment and a team effort across IT, security, and management. If this feels overwhelming, Petronella Technology Group can serve as your guide and support system through all these steps – providing templates, expert advice, technical solutions, and hands-on assistance to implement controls.
Need help getting started? Contact us to schedule a CMMC Readiness Assessment. We’ll evaluate your current state against CMMC requirements and deliver a clear roadmap (gap analysis, POA&M, and recommendations) to achieve compliance. This professional assessment can save you countless hours and ensure you’re on the right track from day one.
Common CMMC Compliance Challenges (and How to Overcome Them)
Implementing CMMC is not without its hurdles. Here are some of the most common challenges defense contractors face on the road to compliance – along with tips for overcoming them:
- Identifying All CUI in Your Organization: One challenge is simply figuring out what information is considered CUI and where it resides. Many businesses are surprised to find CUI hiding in email threads, shared drives, or backups. Solution: Conduct thorough data mapping and classification. Leverage the DoD’s CUI Registry to understand what qualifies as CUI. Train employees to recognize markings and handle CUI properly. It may help to implement a policy that all CUI flows into a designated repository or system. Petronella’s experts can assist by analyzing network shares, emails, and databases for likely CUI keywords and setting up data loss prevention (DLP) tools to catch CUI spillage.
- Resource and Budget Constraints: Small and medium businesses often struggle with the cost of compliance. Meeting CMMC may require new IT investments (tools, software licenses), possibly hiring additional IT/security staff, and the time commitment of existing staff to develop and maintain controls. Solution: Develop a phased budget and seek efficiencies. For instance, instead of building costly infrastructure in-house, use cloud services that are already compliant (e.g., Microsoft GCC High or secure enclaves provided by companies like Petronella). This way you “rent” a secure environment rather than building from scratch. Additionally, look into DoD support programs – sometimes there are grants or assistance for small businesses to improve cybersecurity. Finally, convey to leadership that this is a necessary cost of doing business with DoD. Treat it as an investment that will pay off by keeping contracts and winning new ones.
- Technical Complexity and Legacy Systems: Implementing advanced security controls can be technically challenging, especially if you have older systems that weren’t designed with them in mind. For example, enabling encrypted authentication protocols or modern encryption might be impossible on legacy software. Solution: Modernize and segment. Identify legacy systems that cannot be brought up to standards, and isolate them from CUI or phase them out. Often, migrating to modern platforms (such as updated operating systems, cloud-based services, or newer hardware) is needed. Where legacy tech must remain, compensate with extra controls around it (network segmentation, additional monitoring). Don’t be afraid to seek outside help for complex implementations – e.g., deploying a SIEM or identity management system is complex, but an experienced provider can do it much faster and correctly. Petronella frequently helps clients deploy compliant solutions (like secure authentication systems, logging, etc.) that meet CMMC’s technical demands without reinventing the wheel.
- Developing Documentation and Policies: Many organizations find the documentation requirements to be one of the toughest parts. CMMC (via NIST 800-171) expects formal policies, procedures, and system security plans. Writing these from scratch can be tedious and time-consuming. Solution: Use templates and expert review. Petronella provides policy templates aligned to each CMMC control family – these templates cover the intent of the requirements and can be tailored to your environment. We also provide procedure documents and SSP frameworks. By starting from a solid template, you avoid writer’s block and ensure you don’t miss key elements. Additionally, engage management early to review and approve policies; this ensures buy-in. Once documentation is in place, treat it as living documents – schedule periodic reviews to keep them up to date.
- Employee Awareness and Culture Change: A security program is only as good as the people following it. A common challenge is getting all employees to embrace new practices (like stricter password policies, multi-factor login steps, locking computers, etc.). Some may see it as a nuisance or try to bypass controls. Solution: Emphasize training and communication. Make sure every employee understands why these changes are critical – e.g., explain the stakes of a breach in terms of lost contracts or even national security. Implement engaging security awareness training (not just boring slides). Petronella offers interactive training programs, phishing email simulations, and even quizzes to ensure employees get it. Additionally, get leadership to set the tone – when top management follows all policies and champions security, everyone else is more likely to follow. Recognize and reward good security practices to reinforce the culture.
- Keeping Up with Evolving Requirements: Cybersecurity is not static. NIST 800-171 might be updated (in fact, a Draft Rev.3 is on the horizon), and CMMC policies could evolve. Threats are also always changing. A challenge is maintaining compliance as rules change or as your business changes (e.g., you adopt new technology that needs to be secured). Solution: Treat CMMC compliance as an ongoing program, not a one-time project. Assign a security officer or project manager to continuously monitor for updates – for example, subscribe to DoD and NIST announcements. Consider joining industry groups or forums (the CMMC Information Institute, etc.) for the latest insights. Petronella’s services often include continuous monitoring and quarterly compliance check-ins, to ensure clients don’t fall behind. We keep your documentation updated and systems tuned to new threats, so recertification becomes a breeze.
By proactively addressing these challenges, you can avoid common pitfalls that have tripped up others. It’s normal to hit a snag or two, but with the right partner and plan, each challenge can be managed. Remember, countless defense contractors are going through the same process – you’re not alone, and resources exist to help you.
Benefits of Achieving CMMC Compliance
While CMMC compliance requires effort, it brings significant benefits to your organization beyond the obvious necessity of keeping contracts. Consider the following advantages of being CMMC certified:
- Continued (and Expanded) Business Opportunities: The most direct benefit is that you remain eligible for DoD contracts. You won’t be locked out of bidding due to lack of certification. In fact, being compliant may allow you to bid on new contracts that specify CMMC requirements – giving you access to opportunities competitors might have to pass on. In the long run, CMMC or similar cybersecurity requirements may become standard in other federal agencies and even commercial supply chains. By getting ahead now, you position your company as a preferred supplier in the defense sector and beyond. Compliance can truly be a revenue enabler, not just a cost.
- Stronger Security Posture (Reduced Risk): Implementing the controls in NIST 800-171/172 will greatly improve your cybersecurity maturity. You’ll have better control over your data, improved network defenses, active monitoring for intrusions, and well-trained staff. This means you are less likely to suffer a damaging breach. Even outside of contract requirements, avoiding a cyber incident saves potentially huge costs – downtime, recovery expenses, legal liabilities, loss of customer trust. Compliance effectively “hardens” your organization against threats, which is invaluable in today’s threat landscape.
- Avoidance of Penalties and Liabilities: As discussed, noncompliance can lead to penalties like False Claims Act actions or loss of contracts. By being compliant, you mitigate these legal and financial risks. You won’t have to worry about whistleblowers or DOJ investigations into your cybersecurity claims, because you can prove you’ve done the work. Also, should a breach occur despite your best efforts, being able to show you were compliant with industry-standard security controls could help limit liability (demonstrating you weren’t negligent). It’s similar to having a strong safety program – it can protect you legally if an accident happens despite following best practices.
- Process Improvement and Efficiency: Often in implementing CMMC controls, companies find they streamline their IT and processes. For example, organizing an asset inventory and improving configuration management can lead to more efficient IT operations and fewer unexpected outages. Defining clear procedures for things like user onboarding/offboarding, incident response, or data handling can eliminate ad-hoc chaos and bring consistency. You might also consolidate systems or eliminate redundant software during the process, saving costs. In short, the discipline of meeting these requirements can drive operational maturity and efficiency.
- Trust and Reputation: In the eyes of DoD program managers and prime contractors, a CMMC certification is a sign of trustworthiness and reliability. It shows your company takes protecting sensitive data seriously. You can mention your CMMC compliance in proposals, marketing materials, and discussions – it provides assurance to stakeholders (not just DoD, but potentially other customers) that you value cybersecurity. In an era of frequent news about hacks and ransomware, being able to say “we have met the rigorous CMMC standard” differentiates you. It can even be a selling point to commercial clients who are concerned about the security of their data.
- Future-Proofing: Cyber requirements are only going to become more prevalent. By building a solid cybersecurity foundation now (with CMMC’s help), you’re better prepared for future regulations or higher-level requirements. For instance, if someday a CMMC Level 4 or other advanced framework comes out, you’ll be in a much better position to adapt. Think of compliance as building muscle – once strong, you can handle heavier lifts. Early adopters of CMMC will have a competitive head start if cybersecurity certifications become the norm in other industries or international contracts.
Finally, an often overlooked benefit: peace of mind. As a business owner or executive, knowing that you have taken robust steps to protect your company and meet obligations can help you sleep better at night. Cyber threats and compliance duties can be a big source of stress; achieving compliance alleviates that worry to a large extent. You know you’ve done the right thing to protect both national security and your own enterprise.
Why Choose Petronella Technology Group as Your CMMC Partner
CMMC compliance is a journey – and having the right partner can make that journey smoother, faster, and more successful. Petronella Technology Group (PTG) prides itself on being a leader in cybersecurity and compliance services, with a special focus on helping defense contractors. Here’s why Petronella is the ideal partner for your CMMC efforts:
- Certified CMMC RPO with Expert Staff: Petronella is a CMMC Registered Provider Organization (RPO) certified by the CMMC Accreditation Body (Cyber-AB). This means we are officially recognized for our knowledge in CMMC and adhere to a strict code of professional conduct. Our team includes Registered Practitioners (RPs) who are trained in the CMMC model and NIST standards. When you work with us, you’re getting consultants who thoroughly understand the CMMC requirements and latest updates. We stay current with DoD guidance, interim rules, and best practices so you don’t have to.
- End-to-End Compliance Solutions: We offer a comprehensive suite of services that cover every aspect of CMMC compliance. This includes:
- Gap Assessments & Readiness Reviews: Evaluating your current state against CMMC controls and delivering a detailed remediation plan.
- Policy and Documentation Development: We provide templates and hands-on help to create your SSP, policies, procedures, and all documentation needed for audit. Our packages come with 80% of documentation pre-written, which you can then customize – saving you huge amounts of time.
- Secure Infrastructure & Enclaves: Petronella can design and implement a secure CUI enclave for your data. We have FedRAMP-approved cloud solutions and secure hosting options that meet CMMC requirements. Essentially, we can stand up a compliant IT environment (with proper access controls, monitoring, encryption, etc.) in as little as 30 days, allowing you to fast-track technical compliance.
- Managed Security Services: Compliance is not one-and-done, so we provide ongoing managed services like 24/7 security monitoring (Managed SOC/XDR), vulnerability scanning, and incident response support. Our continuous cybersecurity compliance service helps maintain your CMMC status year-round.
- Training & User Awareness: We deliver customized security training programs that not only meet CMMC requirements (AT-1, AT-2, AT-3) but actually engage your users. From phishing simulations to interactive modules, we help cultivate a security-aware workforce.
- Mock Audits and Audit Support: When you’re nearing your C3PAO assessment, our experts conduct mock audits to ensure you’re fully prepared. During the official audit, we can be by your side to assist with any clarifications the assessors need. Our goal is zero last-minute surprises.
- Proven Track Record: Petronella has successfully guided numerous companies through NIST 800-171 and CMMC compliance. We understand the typical pitfalls (technology, budgeting, cultural) and how to overcome them. Our approach has been refined with real-world experience – we know what auditors look for because we’ve worked on both sides of compliance. Many of our clients have passed their CMMC audits on the first attempt, a testament to our thorough preparation methods. We also have experience across various sectors – from manufacturing to tech – so we can tailor solutions that fit your industry and company size.
- Client-Centric and Personalized Service: We’re not just consultants; we see ourselves as partners invested in your success. Cybersecurity can be complex, so we take time to explain recommendations in plain language and provide options that align with your business goals. Our team truly cares (one of our core values) – as our client, you’re part of the Petronella family and we go the extra mile to help you succeed. Unlike some providers that offer cookie-cutter solutions, we customize our approach to your unique environment. Whether you need full hands-on assistance or just coaching and validation, we adapt to provide the right level of support.
- Rapid Compliance and ROI: We understand that time is of the essence – you have contracts to win and deadlines to meet. Petronella’s methodologies are designed to accelerate compliance. With our “Done-With-You” packages, we can get clients to ~80% compliance in a matter of weeks. We focus on high-impact actions that move the needle. By using our ready-made tools (like secure cloud setups and policy libraries), you save money compared to building everything yourself or through trial-and-error. The faster you get compliant, the sooner you can confidently pursue new business. Many clients find that the cost of our services is offset by efficiency gains and the value of contracts they secure once compliant.
- Beyond Compliance – Security Expertise: Petronella is not just about checking the box. We are a full-fledged cybersecurity firm with capabilities in digital forensics, penetration testing, AI-driven threat detection, and more. This means we bring a depth of technical expertise that ensures your CMMC compliance isn’t superficial – we improve your actual security. If there are underlying weaknesses (like vulnerable web applications or misconfigured networks), we can identify and fix them as part of the engagement. Our holistic approach means you get true security improvement, not just paperwork.
Choosing Petronella means choosing a partner who will guide you from the first steps of compliance all the way through to successful certification and ongoing maintenance. We are passionate about helping companies protect themselves and meet DoD requirements – and we have the credentials and experience to do it right.
Ready to get started? Contact Petronella Technology Group today to schedule a consultation or request our free CMMC 2.0 Guidebook. Let us craft a compliance strategy tailored to your business. With Petronella by your side, you can achieve CMMC 2.0 compliance faster and with greater confidence – turning a challenging mandate into a competitive advantage for your company.
Get in touch with our team now and let’s secure your future in the defense industry.
Download Our Free CMMC 2.0 Guide
Get our step-by-step playbook on how to secure your government contracts, align with NIST 800-171, and prepare for CMMC assessments with confidence.
Why Choose Petronella Technology Group?
 |
Certified CMMC Registered Provider Organization (RPO) We are accredited by the Cyber-AB and help defense contractors get certified quickly, affordably, and without audit failure surprises. |
 |
Done-For-You Compliance Packages 80% of the paperwork is already done. We customize and deploy documentation, policies, SSPs, and POA&Ms for fast-track compliance. |
 |
Secure Hosting & Monitoring Options From GCC High to private enclaves, we offer secure, compliant infrastructure with ongoing XDR and SOC monitoring. |
Schedule Your Free CMMC Readiness Call
Let our certified experts evaluate your SPRS score, readiness gaps, and give you a step-by-step roadmap to pass your CMMC audit the first time.











